Hacks in Wartime: Railroad & Radio Jamming, Industrial Systems Targeted Amid Russia-Ukraine War
Several days of war triggered by the Russian Federation invading Ukraine have led to turmoil in financial markets and new policies barring Russian businesses and aviation from Western countries, while shadowy hacks and ‘information warfare’ add to the chaos.
We took a scan of the high-profile hacking claims and a closer look at a hacked 2GB zip file which contains reams of Russian industrial business procurement data. While the import of this data set is murky, researchers seeking highly structured information on Russia’s industrial base may find it helpful.
Complicating matters, the outbreak of conventional warfare has spurred electronic jamming and ‘Distributed Denial of Service’ (DDoS) attacks where routes are overwhelmed with packets, rendering servers unresponsive. (However some people have had luck using VPNs that provide connections to Russian IP addresses, as defensive geoblocking may be in effect.)
Nuclear risks have intensified in recent days
Radiation readings increased marginally in the immediate environment of the Chernobyl exclusion zone in northern Ukraine, attributed to dust kicked up by invading Russian vehicles. Web-accessible radiation meters have come back online after several days, showing readings returning mostly to normal; they peaked at 92,700 nanosieverts per hour, which is several hundred times higher than background radiation, but the days following the spike are missing data. (Sieverts are ionizing radiation “effective dose” units. This increased rate is comparable to a dental x-ray every hour.)
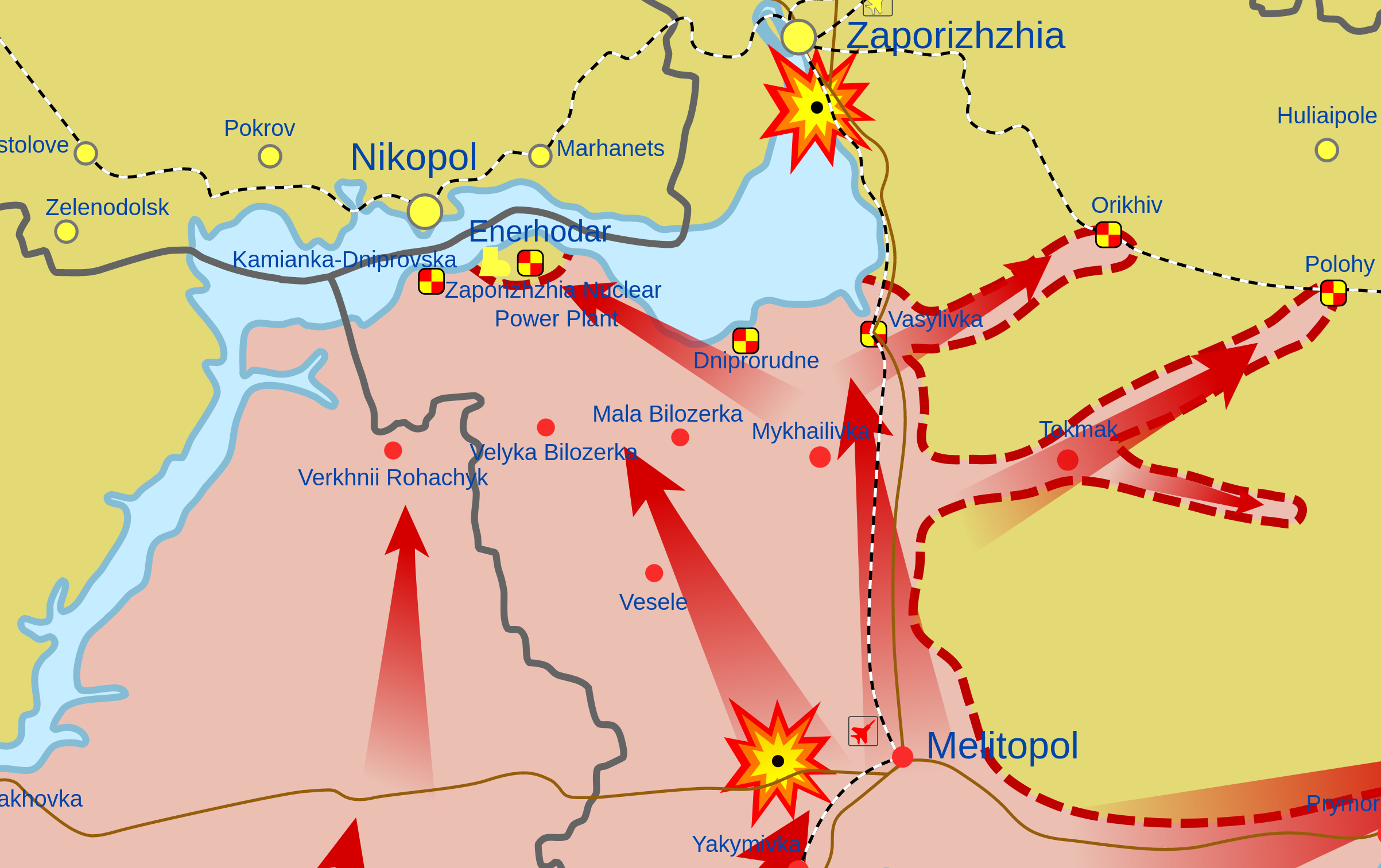
While Chernobyl is dormant, other nuclear power plants (NPP) around Ukraine are still active. While these nuclear stations are engineered to survive aircraft crashes, it is possible that heavy weapons could puncture the containment vessels or break open nearby spent fuel pools. Mycle Schneider, nuclear industry consultant, told Washington Post, “We’ve never seen a full-scale war in a country that operates nuclear facilities.” Six reactors and spent fuel pools at the Zaporizhia NPP complex, north of Crimea, are considered at risk in fighting.
Update: The Zaporizhia Nuclear Power Plant saw a major gun battle overnight during March 3-4. A fire in a training facility was triggered by the battle. See the article : E-SOQPSK Modulation Waveforms for Aeronautical Mobile Telemetry Comms. We streamed the last minutes of the livestream from the site’s administrators before it was knocked offline.
In recent hours, videos from Zaporizhia NPP’s adjacent town, Enerhodar show barricades and masses of residents protesting against imminent Russian occupation. Fencing around a nuclear waste site near Kyiv was also reported damaged in bombardment.
On Feb 28th President Vladimir Putin elevated the alert status of Russia’s strategic nuclear forces, officially calling it a “special mode of combat duty of the deterrence forces.” Dubbed “connecting the wires,” by Russian nuclear force expert Pavel Podvig at the UN Institute for Disarmament Research, this escalated system state increases risks for nuclear war. (Podvig writes that the system is not automated.) At the start of the military operation, Putin made the implicit threat that “No matter who tries to stand in our way or all the more so create threats for our country and our people, they must know that Russia will respond immediately, and the consequences will be such as you have never seen in your entire history.” In terms of strategic nuclear arsenals, this is the most tense geopolitical window the world has seen since the early 1980s.
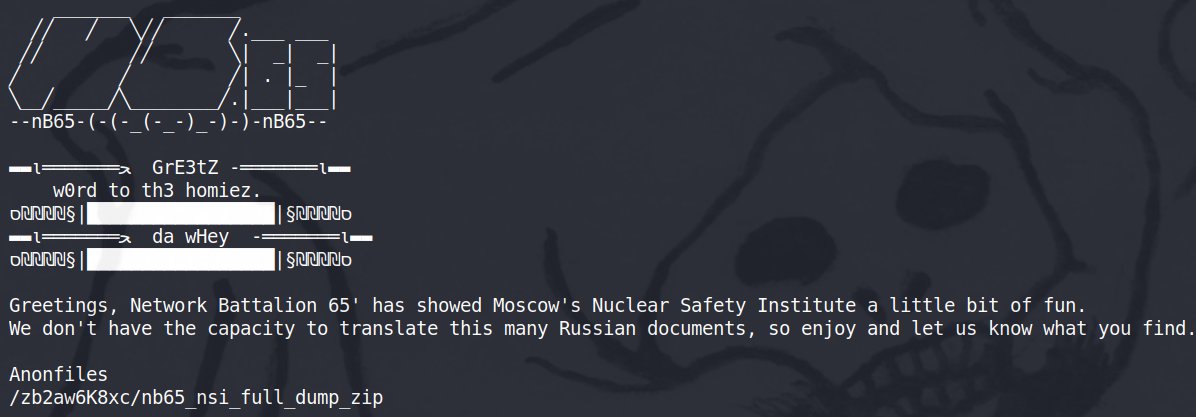
Ostensible “Nuclear Safety Institute” hack
The first Russia-Ukraine war-related hacking claim we examined was a data leak touted in an announcement claimed by “Network Battalion 65” (@xxnb65 – NB65) as originating from the Russian Nuclear Safety Institute of the Academy of Sciences (IBRAE) (we could not confirm its origin). IBRAE, based a couple miles south of Moscow’s Red Square, was established after the Chernobyl disaster in 1988 and partners with the U.S. Department of Energy on some projects and conferences. A site map shows a range of research programs including radioactive waste disposal, atomic particle computer modeling and Arctic environmental research.
IBRAE submits reports to multilateral organizations like the Arctic Council about subjects like communication in nuclear disasters and a chlorine processing facility in Murmansk called Apatityvodokanal, as well as research on decommissioning nuclear submarines and risk modeling. Other research includes nuclear safety, lessons learned in Chernobyl risk communications, simulated meltdown ‘corium’ mixtures, properties of uranium, and nuclear pellet engineering.
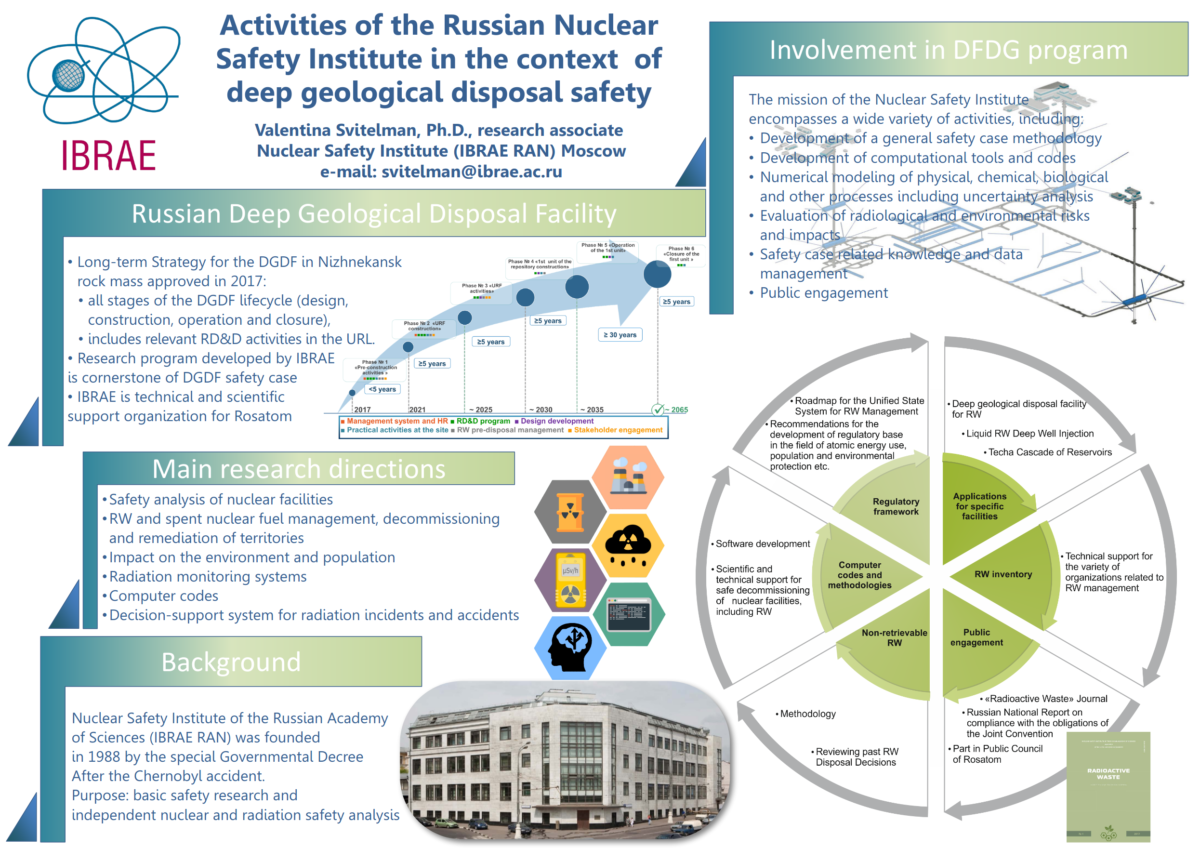
The organization says it has about 540 employees. A slide describes it as a “technical and scientific support organization for ROSATOM”, the enormous Russian state nuclear corporation with more than 270,000 employees.
IBRAE convened an international panel in 2018 on a mysterious radioactive cloud that passed over Europe the year prior, possibly due to an incident at the ‘secretive’ Mayak facility located in the formerly secret city of Chelyabinsk-65; In 1957 Mayak experienced a nuclear accident second only to Chernobyl, with 20 million curies of radioactive substances blown into the atmosphere, known as the Kyshtym disaster. Lake Karachay, within Mayak, is by far the most radioactive open-air location in the world.


The data leak hacking group NB65 claims it got from the Nuclear Safety Institute contains many records on existing businesses that can be crosschecked via ID numbers indexed in Russian corporate transparency websites like list-org.com. It also has indexes of “Business-to-Business” (B2B) web servers for major concerns like Sberbank, (a key target of new Western sanctions) Gazprom, and many others.

Based on many time signatures in the data, the material stretches back several years and was extracted within the last few days.
We have pwned the Nuclear Safety Institute of Moscow, Russia. Stay tuned. #UkraineWar pic.twitter.com/H1qQbLycjW
— NB65 (@xxNB65) February 26, 2022
This system appears to be an enterprise resource planning (ERP) platform, a type of software used to manage internal organizational records such as accounting, supply chain operations etc. [Consultants note that major Russian ERP providers include Galaktika, Parus and 1C, as well as the western giant SAP.]
Among the records are statistics that show how much spending each company received in specific areas, including one specific to atomic energy development (“договоры, заключенные по результатам закупок в области использования атомной энергии”, “contracts concluded as a result of procurement in the field of atomic energy use”). The categories involved seem to be the same as those featured in this document about procurement purchases from small and medium-sized businesses.
The bulk of the files are in the commonly used XML format, which resembles HTML but has customized, nested tags in angle brackets. XML patterns or ‘schemas’ are defined by rule documents referenced by URLs at the top of the XML files. These lead to “zakupki.gov.ru/223fz”. Zakupki is a national-scale procurement system with standardized formatting. Other servers with zakupki in their names are referenced throughout the documents. The number ‘223’ could refer to Russian federal law No 223-FZ governing procurement in public sector entities.
One of the schemas referenced is “zakupki.gov.ru/223fz/dishonestSupplier” which might indicate some kind of anticorruption or bad supplier reference system.
Inside “volumePurchaseData” elements, “customer” cards include registration numbers (iko, inn, kpp, ogrn) which includes various forms of Tax IDs, legal address, postal address, phone, fax and email contact information. It also includes okato, okopf, and okpo which at least in part form regional designators for administrative districts akin to zip codes. Searches for the ‘full name’ and ‘short name’ generate hits about the companies on indexing sites like list-org.com . The “purchaseIndicatorTypeList” has longer phrases for various types of spending which include atomic projects and defense activity as well as more prosaic industrial activity, according to machine translation.
The end of the XML statements include what appear to be public URLs with more data about these vendors, however these URLs are not currently responding, possibly due to widespread DDoS attacks affecting much of the Russian government Internet.
For more information on this realm of procurement data, Transparency.org produced “Tools for conducting civic anti-corruption investigations in the Russian Federation” which addresses the Zakupki system (page 8).

SCADA attacks claimed; Industrial Control Systems probed
The NB65 hacking group also posted a video with 1.2 million views showing what appears to be screen capture of an attack on a “SCADA” (Supervisory Control and Data Acquisition) or industrial control system (ICS) on a natural gas compressor built by Fornovo Gas, altering its operational settings in an attempt to either destroy or destabilize the mechanism.
Attacks on SCADA and ICS systems are regarded as among the most dangerous type of possible hacking operations, because of the risk of explosions, fire, chemical accidents, or similar industrial disasters. NB65 said it is “not our goal” to harm regular Russians.
Fornovo Gas is an Italy-based company which produces natural gas compressors. SCADA attacks on “critical infrastructure” are a major subject of “homeland security” and emergency management research. The Fornovo Gas hack claim was not independently verified.
Looks like the Russian state had a little bit of an issue with their Gas compressor. Can someone say, leaking gas, turned off fans, deleted configurations/profiles, access to the file system & an inevitable shutdown? #Ukraine pic.twitter.com/DnjGJbiUvz
— NB65 (@xxNB65) February 27, 2022
There are strong indications that many parties are looking around for unlocked ICS systems – that is, virtual consoles that can be accessed with ‘VNC’ software which allows direct tampering with industrial systems.
The most famous SCADA/ICS type hacking campaign was Stuxnet, a sophisticated attack with several ‘zero-day’ undisclosed vulnerabilities, widely believed to be designed by U.S. and Israeli intelligence to damage centrifuges used by Iran to generate weapons-grade fissile material.
Belarus railway hacking campaign claimed
Belarus, a client state of Russia controlled by President Alexander Lukashenko since 1994, has been key to the conflict. Ukrainians have claimed Belarussian units have been among invading forces streaming over the border, however Western governments and Belarus itself refuted this, as of March 1. In 2012 Reuters interview Lukashenko described himself as the “last dictator in Europe.”
The “Belarusian Cyber Partisans” (@cpartisans) have claimed several times to interfere with Belarus’ antiquated railroad technology which has been critical to the Russian Federation’s deployments before and during the invasion. Most recently they claimed to stop rail traffic in several cities by exploiting Windows XP vintage platforms.
Today the Belarusian Cyber-Partisons group (@cpartisans) staged a cyber attack against the Belarusian railway infrastructure, designed to halt Russian military movements. Trains stopped in Minsk, Orsha, and Osipovichi
The railway system uses Windows XP.
Image via @cpartisans. pic.twitter.com/Rr0dkD0eD0— vx-underground (@vxunderground) February 28, 2022
Belarus arms manufacturer hacked, emails & documents released
A Belarusian weapons manufacturer got hacked and over 200 gigabytes of internal emails were released, delivering a more tangible result than the other ‘hacktivist’ claims we looked at. The nonprofit transparency collective Distributed Denial of Secrets has made this archive available to researchers:
Over 200 gigabytes of emails from the Belarusian weapons manufacturer Tetraedr. Tetraedr has operated since 2001 and offers missile and gun systems, air defense and surveillance radar systems, specialist training, as well as system repair and upgrades.
The release consists of two parts. The first part is the most recent 1,000 emails from each inbox, in .EML format. The second part is a complete archive of each inbox in .PST format, though the hackers note that some .PST files may have corruption issues resulting from the export process.
The hackers identify themselves as Anonymous Liberland and the Pwn-Bär Hack Team on a .onion website which quietly began circulating and posted the data in late February 2022. The site announced their opposition to Putin, Russia and CIS countries.
Journalists investigating the data found videos of weapons tests and weapons schematics among the files leaked.
Just a sample of some of the data from the Belarusian weapons manufacturer Tetraedr, whose emails were allegedly hacked and leaked by “Anonymous Liberiand” and “The Pen-Bär Hack Team.” pic.twitter.com/ZgvNUOKmCE
— Mikael Thalen (@MikaelThalen) February 26, 2022
DDoSecrets prudently noted due to the complicated wartime situation, “there is an increased chance of malware, ulterior motives and altered or implanted data, or false flags/fake personas.” Such drops should not be opened on computers that haven’t been “hardened” to prevent the effects of malware or viruses.
Given the choppy state of the information seas, one security specialist @neurovagrant provided a useful list of basic security tips anyone can apply to reduce the risks of malicious activity. UC Berkeley, CISA.gov and the Electronic Frontier Foundation also have a wealth of vetted digital security advice.
Tango Down: The “IT Army of Ukraine” (@ITarmyUA) has been touting Anonymous-style DDoS jamming campaigns and other hacking activity:
https://twitter.com/ITarmyUA/status/1498050357792063490
YourAnonNews (YAN), a long-standing clearinghouse for “Anonymous” campaign activity, asserts that the redoubtable, vaguely defined hack crew swarm has launched a “cyber war” against Russia due to the Ukraine invasion. YAN also attributed the gas compressor hack to “Anonymous” while quoting NB65. @DeepNetAnon gave out a list of “targets” including major Russian banks and other key industries.
Get yer botnetz and join us.#Anonymous is currently engaged in a full-blown cyber war against the Russian government and Putin's murderous war machine. pic.twitter.com/dFKWUKopMM
— Anonymous (@YourAnonNews) February 26, 2022
Insertions of Ukrainian images into Russian TV channels were also reported, including insertion of pro-Ukrainian songs, and videos showing the invasion.
Rise of the Ham Radio Jammers
In recent weeks interference with radio transmissions on Russian military bands has become more widely reported, with do-it-yourself electronic countermeasures (ECM) and pirate signals jamming standard use. As with many other tactics this has been attributed to “Anonymous.” In January Janus Rose reported that the enigmatic and infamous Russian shortwave station UVB-76, which has broadcast cryptic number codes for decades, has recently been bombarded with all sorts of memes, including songs like “Gangnam Style” and memes that appear on spectrum analyzer displays.
On March 1 more radio recordings were released that show jammers interrupting Russian Federation military comms and playing music. Many Russian forces seem to lack encrypted radios, which enables radio hobbyists to listen in and inject their own signals. Day by day, jamming has been intensifying, according to observers.
The WebSDR website permits tuning into a range of frequencies from various receivers via web browsers. Strange distorted voices and music could be heard via a shortwave receiver run by the ETGD amateur radio club at the University of Twente in the Netherlands. (This website tracks shortwave broadcasts.)
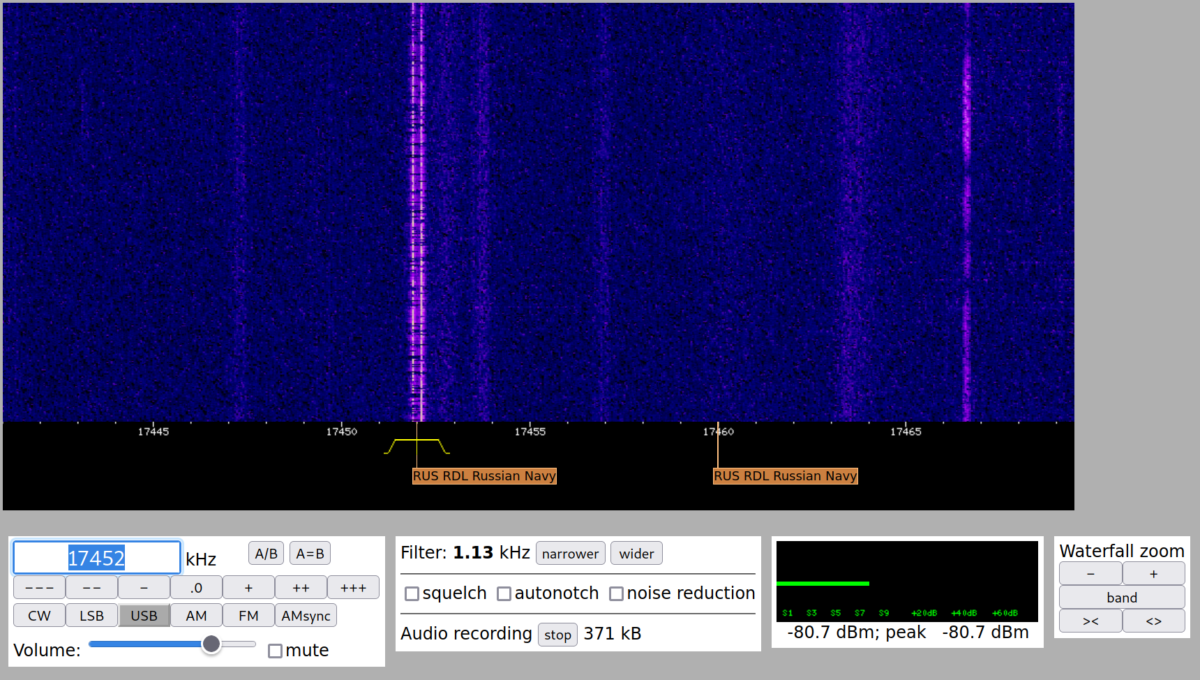
Software defined radios (SDRs) are a versatile and increasingly affordable technology. Lots of bands can be investigated with simple adapters and cheap or free software. (More info: 1, 2, 3, 4)
Last year Unicorn Riot looked at how to detect unmarked FBI surveillance planes using SDRs.
El denominado "The Buzzer" (UVB-76) un sistema de radiocomunicaciones militares rusas desde hace casi 40 años, lleva días interferido por "piratas". Muchos vinculan esta actividad con el conflicto de Ucrania. La pasada noche se emitieron imágenes muy bizarras en su frecuencia👇👇 pic.twitter.com/5QOMKPtIA1
— David Marugán (@RadioHacking) January 20, 2022
“Cyberknow” compiled a table of claimed hack crews on all sides of the conflict.

Nuclear War, Exercises and Hacking: “A Strange Game”
The 1983 movie WarGames, about a young hacker nearly setting off a nuclear war with the Soviet Union, caused such a stir in Washington that it led to the Computer Fraud and Abuse Act (CFAA), a draconian measure which is still law today. Things have almost come full circle as the world once again contemplates nuclear war, where “the only winning move is not to play,” as an AI famously declares in the film.
Global nuclear tensions are now at a peak not seen since the 1983 NATO exercise “ABLE ARCHER” nearly convinced the aging Soviet leadership that an American attack was imminent. Declassified ABLE ARCHER documents are available at the National Security Archive.
Only limited information is available about the 1982 nuclear wargame exercise series IVY LEAGUE 82/NINE LIVES/REX 82 ALPHA, which simulated a major nuclear exchange and highly secret “continuity of government” (COG) procedures involving the Federal Emergency Management Agency (FEMA). President Jimmy Carter’s classified 1980 directive, PD-59, likely intensified the early 1980s climate of nuclear tension. (PD-59 is even a plot point in the BBC’s 1985 Thatcher-era nuclear noir series “Edge of Darkness.”)
Inside the United States, 18 U.S. Code § 1030 governs computer access law: “exceeding authorized access” has long been the magic term applied by federal prosecutors in hacking cases. We have heard that at least on a formal level, U.S. federal government employees are constrained by “standard operating procedures” (SOP) from freelancing ‘offensive’ operations without prior approval, a policy aimed at preventing government infosec types from going on the offensive on their own time. The wild electronic high frontier in the Russia-Ukraine war may likely color the outcome of any reforms of ‘offensive’ hacking rules.
Calls to detach Russia from Internet architecture
Like many other ‘behind the scenes’ aspects of global infrastructure, the international organizations that manage Internet routing and network designations have also been touched by the Russian invasion of Ukraine. Ukrainian officials have submitted requests to remove Russia’s root Domain Name Servers from authority, and remove the root domains of .RU and .SU (Yes, the Soviet Union has a two-letter domain country code which is still used to this day to host websites, under the direction of Russian internet authorities.)
I’m strongly asking you to introduce the following list of sanctions targeting Russian Federation’s access to the Internet: Revoke, permanently or temporarily, the domains “.ru”, “.рф” and “.su”. This list is not exhaustive and may also include other domains issued in the Russian Federation. […]
Shut down DNS root servers situated in the Russian Federation, namely:
Saint Petersburg, RU (IPv4 199.7.83.42)
Moscow, RU (IPv4 199.7.83.42, 3 instances)Apart from these measures, I will be sending a separate request to RIPE NCC asking to withdraw the right to use all IPv4 and IPv6 addresses by all Russian members of RIPE NCC (LIRs – Local Internet Registries), and to block the DNS root servers that it is operating.
Andrii Nabok, Representative of Ukraine in GAC ICANN (Source: ICANN mailing list)
A detailed report on DataCenterDynamics outlines how Russia’s capture and annexation of Crimea in 2014 was followed by takeovers of Internet routing and overall Internet control.
Furthermore, Russian authorities appeared to practice ‘disconnecting’ from the Internet entirely during tests in June and July 2021. Some observers believe that this could intensify the fracturing of the global Internet into national fiefdoms with something akin to the “Great Chinese Firewall” managing access between Russia and the outside world.
On a related note, routing concerns have led the U.S. Federal Communications Commission (FCC) to warn of attacks that may affect ‘Border Gateway Protocol’ to redirect traffic, combined with botnets to cause DDoS attacks. The FCC has requested industry comments about steps it “should take to protect the nation’s communications network from vulnerabilities posed by the Border Gateway Protocol”.
Prank on Putin’s Yacht
On Saturday, Feb 26, 2022, ‘Anonymous’ pranksters tampering with maritime Automated Identification Systems (AIS) data caused Putin’s yacht to appear to run aground or crash into Snake Island, a strategic location in Ukrainian territorial waters of the Black Sea. The Yacht’s supposed estimated arrival time was set for April Fools Day, with the callsign reading “FCKPTN.”
Snake Island was also where Ukrainian border personnel were initially claimed killed, although that has now been retracted, it was later reported that dozens of Ukranian personnel were captured. AIS has been faked in this region before: Falsified AIS appeared to show HMS Defender (destroyer) and HNLMS Evertsen (missile frigate) approach Sevastopol, Crimea, on June 19, 2021 – it appeared as if they approached the Russian naval base from Odessa, Ukraine.
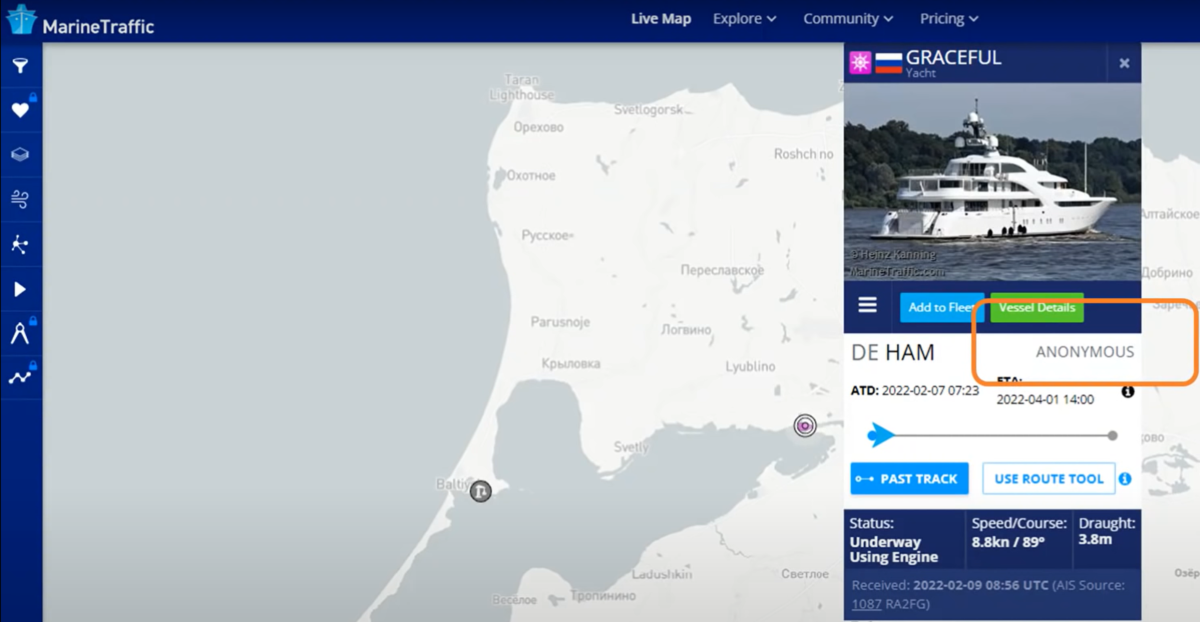
While it’s very difficult to verify electronic hacks and interference with technical systems, the heated wartime environment has motivated lots of people to jump into action, and forms of evidence like file and email datasets (like the ‘Tetraedr’ hack) promise to give a more firm picture as events unfold.
Correction: Mycle Schneider, not the IAEA, told the Washington Post, that a conventional war has never been fought in a country with nuclear power stations.
Please consider a tax-deductible donation to help sustain our horizontally-organized, non-profit media organization:
Follow us on Twitter, Facebook, YouTube, Vimeo, Instagram, and Patreon.






Comments are closed.